
Network
Computer Network
An interconnection of multiple devices, also known as hosts, that are connected using multiple paths for
the
purpose of sending/receiving data or media. Computer networks can also include multiple devices/mediums
which help in the communication between two different devices; these are known as Network devices and
include things such as routers, switches, hubs, and bridges.
A computer network is a set of devices connected through links. A node can be computer, printer, or any
other device capable of sending or receiving the data. The links connecting the nodes are known as
communication channels.
Computer Network is a group of computers connected with each other through wires, optical fibres or
optical
links so that various devices can interact with each other through a network.
The aim of the computer network is the sharing of resources among various devices.
In the case of computer network technology, there are several types of networks that vary from simple to
complex level.
Computer Network uses distributed processing in which task is divided among several computers. Instead,
a
single computer handles an entire task, each separate computer handles a subset
Advantages of Distributed processing
Security
Faster problem solving
Security through redundancy
Components Of Computer Network
NIC(National interface card)
A network interface card (NIC) is a hardware component without which a computer cannot be connected over
a
network. It is a circuit board installed in a computer that provides a dedicated network connection to
the
computer. It is also called network interface controller, network adapter or LAN adapter.
NIC is a device that helps the computer to communicate with another device. The network interface card
contains the hardware addresses, the data-link layer protocol use this address to identify the system on
the
network so that it transfers the data to the correct destination.
NIC allows both wired and wireless communications.
NIC allows communications between computers connected via local area network (LAN) as well as
communications
over large-scale network through Internet Protocol (IP).
NIC is both a physical layer and a data link layer device, i.e. it provides the necessary hardware
circuitry
so that the physical layer processes and some data link layer processes can run on it.
NIC cards are of two types − Internal & External
Every computer on a network, both clients and servers, requires a network interface card (or NIC) in
order
to access the network. A NIC is usually a separate adapter card that slides into one of the server’s
motherboard expansion slots. However, most newer computers have the NIC built into the motherboard, so a
separate card isn’t needed
Internal Network Cards
In internal networks cards, motherboard has a slot for the network card where it can be inserted. It
requires network cables to provide network access. Internal network cards are of two types. The first
type
uses Peripheral Component Interconnect (PCI) connection, while the second type uses Industry Standard
Architecture (ISA).
PCI NICs fit into a PCI slot on a motherboard. ISA NICs fit into an ISA slot.
ISA and PCI Compared
For many years, ISA and PCI were equivalents. Because PCI was introduced as a complement to, rather than
a
direct competitor to ISA, it is not uncommon for motherboards to have both ISA and PCI ports. ISA, at
least
for a time, was concurrent with the PCI standard. ISA would give better performance in some areas, while
PCI
yielded better performance in other areas.
In physical appearance the ISA and PCI ports are vastly different. The ISA is longer (by about two
inches),
and thus the I/O cards that connect via ISA tend to be bulkier as well. Their differences do not stop
there.
PCI is a significantly faster (in theory) bus. PCI has double (or in rare instances, quadruple) the
bit-width, resulting in faster data transfer.
When placed head-to-head, PCI is definitely the better and faster option. Which is to be expected,
considering PCI is a full ten years newer. While, in 2010, ISA is practically obsolete and PCI is well
on
its way to extinction as PCI-E and Mini-PCI-E gain steam, they are still in use by many consumers and
industries. ISA and PCI made a significant impact on the computer industry.
External Network Cards
In desktops and laptops that do not have an internal NIC, external NICs are used. External network cards are of two types: Wireless and USB based. Wireless network card needs to be inserted into the motherboard, however no network cable is required to connect to the network. They are useful while traveling or accessing a wireless signal.
Hub
Hub is a central device that splits the network connection into multiple devices. When computer requests
for
information from a computer, it sends the request to the Hub. Hub distributes this request to all the
interconnected computers
A hub is a physical layer networking device which is used to connect multiple devices in a network. They
are
generally used to connect computers in a LAN.
A hub has many ports in it. A computer which intends to be connected to the network is plugged in to one
of
these ports. When a data frame arrives at a port, it is broadcast to every other port, without
considering
whether it is destined for a particular destination or not.
They operate in the physical layer of the OSI model.
It is a non-intelligent network device that sends message to all ports.
It primarily broadcasts messages.
Transmission mode is half duplex.
Collisions may occurs during setup of transmission when more than one computers place data
simultaneously in
the corresponding ports.
They are passive devices, they don’t have any software associated with it.
They generally have fewer ports of 4/12.
switches
Switch is a networking device that groups all the devices over the network to transfer the data to
another
device. A switch is better than Hub as it does not broadcast the message over the network, i.e., it
sends
the message to the device for which it belongs to. Therefore, we can say that switch sends the message
directly from source to the destination.
A switch is a data link layer networking device which connects devices in a network and uses packet
switching to send and receive data over the network.
Like a hub, a switch also has many ports, to which computers are plugged in. However, when a data frame
arrives at any port of a network switch, it examines the destination address and sends the frame to the
corresponding device(s). Thus, it supports both unicast and multicast communications.
They operate in the data link layer of the OSI model.
It is an intelligent network device that sends message to selected destination ports.
Transmission mode is full duplex.
Collisions do not occur since the communication is full duplex.
They are active devices, equipped with network software.
The number of ports is higher – 24/48.
Cables and connectors
Cable is a transmission media that transmits the communication signals. There are three types of cables:
Twisted pair cable:
It is a high-speed cable that transmits the data over 1Gbps or more.
One of the earliest guided transmission media is twisted pair cables. A twisted pair cable comprises of
two
separate insulated copper wires, which are twisted together and run in parallel. The copper wires are
typically 1mm in diameter. One of the wires is used to transmit data and the other is the ground
reference.
Reason for Twisting -
All transmissions are prone to noise, interferences, and crosstalks. When the wires are twisted, some
part
of the noise signals is in the direction of data signals while the other parts are in the opposite
directions. Thus the external waves cancel out due to the different twists. The receiver calculates the
difference in the voltages of the two wires for retrieving data. Thus a much better immunity against
noise
is obtained.
Applications of Twisted-Pair Cables -
In telephone lines,
In DSL lines,
In LANs.
There are two types of twisted pair cables −
Unshielded Twisted Pair ( UTP ): These generally comprise of wires and insulators.
Shielded Twisted Pair ( STP ): They have a braided wired mesh that encases each pair of insulated
wires.
EIA has classified twisted pair cables into seven categories
Coaxial cable:
Coaxial cable resembles like a TV installation cable. Coaxial cable is more expensive than
twisted pair cable, but it provides the high data transmission speed.
Coaxial cables, commonly called coax, are copper cables with metal shielding designed to provide
immunity
against noise and greater bandwidth. Coax can transmit signals over larger distances at a higher speed
as
compared to twisted pair cables.
Coax has a central core of stiff copper conductor for transmitting signals. This is covered by an
insulating
material. The insulator is encased by a closely woven braided metal outer conductor that acts as a
shield
against noise. The outer conductor is again enclosed by a plastic insulating cover.
Coaxial cables are categorized into three types as per radio government (RG) ratings - RG – 59, RG – 58,
RG
– 11
Applications of Coaxial Cables -
In analog telephone networks: A single coaxial network can carry about 10,000 voice signals.
In digital telephone networks: A coax has a data rate of 600 Mbps.
In cable TV networks
In traditional Ethernet LANs
In MANs
Fibre optic cable:
Fibre optic cable is a high-speed cable that transmits the data using light beams. It
provides high data transmission speed as compared to other cables. It is more expensive as compared to
other
cables, so it is installed at the government level.
Optical fiber cables are transparent, flexible fibers made up of glass or plastic through which light
waves
can pass
Structure of a Fiber – Optic Cable
A cross section of a fiber optic cable reveals three parts −
Core − It is the innermost portion of an optical fiber through which light propagates. It is cylindrical
in
shape and it made up of a flexible glass of high refractive index. The diameter of the core of a single
mode
fiber is 8 – 10 μm while multimode fibers are 50 μm in diameter. It is also called the optical waveguide
since it is the main channel through which light signals are transmitted.
Cladding − The core is surrounded by a glass cladding. The glass of cladding has a lower refractive
index
than the core. This enables total internal reflection of light waves in the core, and eventually
propagation
of light waves within the core.
Outer Coating or Jacket − The outer jacket is a thin plastic sheath or coating that is opaque to light.
It
prevents light rays from outside to enter the optical fiber. Fibers are typically bundles together,
where
each bundle is covered by a protective outer sheath that prevents the fibers from physical damage.
There are two types of fibers −
Step-index fiber : In these, the refractive index of the core is constant and undergoes an abrupt change
at
the interface with the cladding.
Graded-index fiber: The refractive index of the core varies in a radial manner from the center. The
fiber is
densest at the core and becomes rarer towards the edge of the core.
Both of these are further divided into two categories depending upon propagation modes of the fibers −
Single-mode fiber
Multi-mode fiber
Router
Router is a device that connects the LAN to the internet. The router is mainly used to connect the
distinct
networks or connect the internet to multiple computers.
Routers are networking devices operating at layer 3 or a network layer of the OSI model. They are
responsible for receiving, analysing, and forwarding data packets among the connected computer networks.
When a data packet arrives, the router inspects the destination address, consults its routing tables to
decide the optimal route and then transfers the packet along this route.
Features of Routers
A router is a layer 3 or network layer device.
It connects different networks together and sends data packets from one network to another.
A router can be used both in LANs (Local Area Networks) and WANs (Wide Area Networks).
It transfers data in the form of IP packets. In order to transmit data, it uses IP address mentioned in
the
destination field of the IP packet.
Routers have a routing table in it that is refreshed periodically according to the changes in the
network.
In order to transmit data packets, it consults the table and uses a routing protocol.
In order to prepare or refresh the routing table, routers share information among each other.
Routers provide protection against broadcast storms.
Routers are more expensive than other networking devices like hubs,bridges and switches.
Routers are manufactured by some popular companies like −
Cisco
D-Link
HP
3Com
Juniper
Nortel
Routing Table
The functioning of a router depends largely upon the routing table stored in it. The routing table
stores
the available routes for all destinations. The router consults the routing table to determine the
optimal
route through which the data packets can be sent.
A routing table typically contains the following entities −
IP addresses and subnet mask of the nodes in the network
IP addresses of the routers in the network
Interface information among the network devices and channels
Routing tables are of two types −
Static Routing Table − Here, the routes are fed manually and are not refreshed automatically. It is
suitable
for small networks containing 2-3 routers.
Dynamic Routing Table − Here, the router communicates with other routers using routing protocols to
determine the available routes. It is suited for larger networks having large number of routers.
Types of Routers
A variety of routers are available depending upon their usages. The main types of routers are −
Wireless Router − They provide WiFi connection WiFi devices like laptops, smartphones etc. They can also
provide standard Ethernet routing. For indoor connections, the range is 150 feet while its 300 feet for
outdoor connections.
Broadband Routers − They are used to connect to the Internet through telephone and to use voice over
Internet Protocol (VoIP) technology for providing high-speed Internet access. They are configured and
provided by the Internet Service Provider (ISP).
Core Routers − They can route data packets within a given network, but cannot route the packets between
the
networks. They helps to link all devices within a network thus forming the backbone of network. It is
used
by ISP and communication interfaces.
Edge Routers − They are low-capacity routers placed at the periphery of the networks. They connect the
internal network to the external networks, and are suitable for transferring data packets across
networks.
They use Border Gateway Protocol (BGP) for connectivity. There are two types of edge routers, subscriber
edge routers and label edge routers.
Brouters − Brouters are specialised routers that can provide the functionalities of bridges as well.
Like a
bridge, brouters help to transfer data between networks. And like a router, they route the data within
the
devices of a network.
Modem
Modem connects the computer to the internet over the existing telephone line. A modem is not integrated
with the computer motherboard. A modem is a separate part on the PC slot found on the motherboard.
The data stored on the computer is digital whereas a telephone line or cable wire can transmit only
analog data.
The main function of the modem is to convert digital signal into analog and vice versa. Modem is a
combination of two devices − modulator and demodulator. The modulator converts digital data into analog
data when the data is being sent by the computer. The demodulator converts analog data signals into
digital data when it is being received by the computer.
Depending on direction of data transmission, modem can be of these types −
Simplex − A simplex modem can transfer data in only one direction, from digital device to network
(modulator) or network to digital device (demodulator).
Half duplex − A half-duplex modem has the capacity to transfer data in both the directions but only one
at a time.
Full duplex − A full duplex modem can transmit data in both the directions simultaneously.
Modem is abbreviation for Modulator – De-modulator. Modems are used for data transfer from one computer
network to another computer network through telephone lines. The computer network works in digital mode,
while analog technology is used for carrying massages across phone lines.
Modulator converts information from digital mode to analog mode at the transmitting end and de-modulator
converts the same from analog to digital at receiving end. The process of converting analog signals of
one computer network into digital signals of another computer network so they can be processed by a
receiving computer is referred to as digitizing.
When an analog facility is used for data communication between two digital devices called Data Terminal
Equipment (DTE), modems are used at each end. DTE can be a terminal or a computer.
The modem at the transmitting end converts the digital signal generated by DTE into an analog signal by
modulating a carrier. This modem at the receiving end demodulates the carrier and hand over the
demodulated digital signal to the DTE.
The transmission medium between the two modems can be dedicated circuit or a switched telephone circuit.
If a switched telephone circuit is used, then the modems are connected to the local telephone exchanges.
Whenever data transmission is required connection between the modems is established through telephone
exchanges.
Computer Network Architecture
Computer Network Architecture is defined as the physical and logical design of the software, hardware,
protocols, and media of the transmission of data. Simply we can say that how computers are organized and
how
tasks are allocated to the computer.
The two types of network architectures are used:
Peer-To-Peer network
Client/Server Network
Peer-To-Peer network
Peer-To-Peer network is a network in which all the computers are linked together with equal privilege
and
responsibilities for processing the data.
Peer-To-Peer network is useful for small environments, usually up to 10 computers.
Peer-To-Peer network has no dedicated server.
Special permissions are assigned to each computer for sharing the resources, but this can lead to a
problem
if the computer with the resource is down.
Advantages Of Peer-To-Peer Network:
It is less costly as it does not contain any dedicated server.
If one computer stops working but, other computers will not stop working.
It is easy to set up and maintain as each computer manages itself.
Disadvantages Of Peer-To-Peer Network:
In the case of Peer-To-Peer network, it does not contain the centralized system . Therefore, it
cannot
back up the data as the data is different in different locations.
It has a security issue as the device is managed itself.
Client/Server Network
Client/Server network is a network model designed for the end users called clients, to access the
resources
such as songs, video, etc. from a central computer known as Server.
The central controller is known as a server while all other computers in the network are called
clients.
A server performs all the major operations such as security and network management.
A server is responsible for managing all the resources such as files, directories, printer, etc.
All the clients communicate with each other through a server. For example, if client1 wants to send some
data to client 2, then it first sends the request to the server for the permission. The server sends the
response to the client 1 to initiate its communication with the client 2.
Advantages Of Client/Server network:
A Client/Server network contains the centralized system. Therefore we can back up the data easily.
A Client/Server network has a dedicated server that improves the overall performance of the whole
system.
Security is better in Client/Server network as a single server administers the shared resources.
It also increases the speed of the sharing resources.
Disadvantages Of Client/Server network:
Client/Server network is expensive as it requires the server with large memory.
A server has a Network Operating System(NOS) to provide the resources to the clients, but the cost of
NOS is very high.
It requires a dedicated network administrator to manage all the resources.
Topology
- Bus
- Ring
- Tree
- Star
- Mesh
- Hybrid
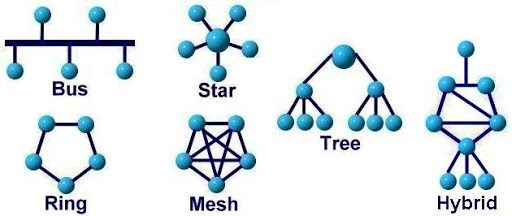
Bus Topology
The bus topology is designed in such a way that all the stations are connected through a single cable
known as a backbone cable.
Each node is either connected to the backbone cable by drop cable or directly connected to the backbone
cable.
When a node wants to send a message over the network, it puts a message over the network. All the
stations available in the network will receive the message whether it has been addressed or not.
The bus topology is mainly used in 802.3 (ethernet) and 802.4 standard networks.
The configuration of a bus topology is quite simpler as compared to other topologies.
The backbone cable is considered as a "single lane" through which the message is broadcast to all the
stations.
The most common access method of the bus topologies is CSMA (Carrier Sense Multiple Access).
CSMA: It is a media access control used to control the data flow so that data integrity is
maintained,
i.e., the packets do not get lost. There are two alternative ways of handling the problems that occur
when two nodes send the messages simultaneously.
CSMA CD: CSMA CD (Collision detection) is an access method used to detect the collision. Once the
collision is detected, the sender will stop transmitting the data. Therefore, it works on "recovery
after the collision".
CSMA CA: CSMA CA (Collision Avoidance) is an access method used to avoid the collision by
checking
whether the transmission media is busy or not. If busy, then the sender waits until the media becomes
idle. This technique effectively reduces the possibility of the collision. It does not work on "recovery
after the collision".
Advantages of Bus topology:
Low-cost cable: In bus topology, nodes are directly connected to the cable without passing through a
hub. Therefore, the initial cost of installation is low.
Moderate data speeds: Coaxial or twisted pair cables are mainly used in bus-based networks that support
upto 10 Mbps.
Familiar technology: Bus topology is a familiar technology as the installation and troubleshooting
techniques are well known, and hardware components are easily available.
Limited failure: A failure in one node will not have any effect on other nodes.
Disadvantages of Bus topology:
Extensive cabling: A bus topology is quite simpler, but still it requires a lot of cabling.
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any
fault occurs in the cable, then it would disrupt the communication for all the nodes.
Signal interference: If two nodes send the messages simultaneously, then the signals of both the nodes
collide with each other.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Attenuation: Attenuation is a loss of signal leads to communication issues. Repeaters are used to
regenerate the signal.
Ring Topology
Ring topology is like a bus topology, but with connected ends.
The node that receives the message from the previous computer will retransmit to the next node.
The data flows in one direction, i.e., it is unidirectional.
The data flows in a single loop continuously known as an endless loop.
It has no terminated ends, i.e., each node is connected to other node and having no termination point.
The data in a ring topology flow in a clockwise direction.
The most common access method of the ring topology is token passing.
Token passing: It is a network access method in which token is passed from one node to another node.
Token: It is a frame that circulates around the network.
Working of Token passing
A token moves around the network, and it is passed from computer to computer until it reaches the
destination.
The sender modifies the token by putting the address along with the data.
The data is passed from one device to another device until the destination address matches. Once the
token received by the destination device, then it sends the acknowledgment to the sender.
In a ring topology, a token is used as a carrier.
Advantages of Ring topology:
Network Management: Faulty devices can be removed from the network without bringing the network
down.
Product availability: Many hardware and software tools for network operation and monitoring are
available.
Cost: Twisted pair cabling is inexpensive and easily available. Therefore, the installation cost is very
low.
Reliable: It is a more reliable network because the communication system is not dependent on the single
host computer.
Disadvantages of Ring topology:
Difficult troubleshooting: It requires specialized test equipment to determine the cable faults. If any
fault occurs in the cable, then it would disrupt the communication for all the nodes.
Failure: The breakdown in one station leads to the failure of the overall network.
Reconfiguration difficult: Adding new devices to the network would slow down the network.
Delay: Communication delay is directly proportional to the number of nodes. Adding new devices increases
the communication delay.
Star Topology
Star topology is an arrangement of the network in which every node is connected to the central hub,
switch or a central computer.
The central computer is known as a server, and the peripheral devices attached to the server are known
as clients.
Coaxial cable or RJ-45 cables are used to connect the computers.
Hubs or Switches are mainly used as connection devices in a physical star topology.
Star topology is the most popular topology in network implementation.
Advantages of Star topology
Efficient troubleshooting: Troubleshooting is quite efficient in a star topology as compared to bus
topology. In a bus topology, the manager has to inspect the kilometers of cable. In a star topology, all
the stations are connected to the centralized network. Therefore, the network administrator has to go to
the single station to troubleshoot the problem.
Network control: Complex network control features can be easily implemented in the star topology. Any
changes made in the star topology are automatically accommodated.
Limited failure: As each station is connected to the central hub with its own cable, therefore failure
in one cable will not affect the entire network.
Familiar technology: Star topology is a familiar technology as its tools are cost-effective.
Easily expandable: It is easily expandable as new stations can be added to the open ports on the
hub.
Cost effective: Star topology networks are cost-effective as it uses inexpensive coaxial cable.
High data speeds: It supports a bandwidth of approx 100Mbps. Ethernet 100BaseT is one of the most
popular Star topology networks.
Disadvantages of Star topology
A Central point of failure: If the central hub or switch goes down, then all the connected nodes will
not be able to communicate with each other.
Cable: Sometimes cable routing becomes difficult when a significant amount of routing is required.
Tree topology
Tree topology combines the characteristics of bus topology and star topology.
A tree topology is a type of structure in which all the computers are connected with each other in
hierarchical fashion.
The top-most node in tree topology is known as a root node, and all other nodes are the descendants of
the root node.
There is only one path exists between two nodes for the data transmission. Thus, it forms a parent-child
hierarchy.
Advantages of Tree topology
Support for broadband transmission: Tree topology is mainly used to provide broadband transmission,
i.e., signals are sent over long distances without being attenuated.
Easily expandable: We can add the new device to the existing network. Therefore, we can say that tree
topology is easily expandable.
Easily manageable: In tree topology, the whole network is divided into segments known as star networks
which can be easily managed and maintained.
Error detection: Error detection and error correction are very easy in a tree topology.
Limited failure: The breakdown in one station does not affect the entire network.
Point-to-point wiring: It has point-to-point wiring for individual segments.
Disadvantages of Tree topology
Difficult troubleshooting: If any fault occurs in the node, then it becomes difficult to troubleshoot
the problem.
High cost: Devices required for broadband transmission are very costly.
Failure: A tree topology mainly relies on main bus cable and failure in main bus cable will damage the
overall network.
Reconfiguration difficult: If new devices are added, then it becomes difficult to reconfigure.
Mesh topology
Mesh technology is an arrangement of the network in which computers are interconnected with each other
through various redundant connections.
There are multiple paths from one computer to another computer.
It does not contain the switch, hub or any central computer which acts as a central point of
communication.
The Internet is an example of the mesh topology.
Mesh topology is mainly used for WAN implementations where communication failures are a critical
concern.
Mesh topology is mainly used for wireless networks.
Mesh topology can be formed by using the formula:
Number of cables = (n*(n-1))/2;
Where n is the number of nodes that represents the network.
Mesh topology is divided into two categories:
Fully connected mesh topology
Partially connected mesh topology
Full Mesh Topology: In a full mesh topology, each computer is connected to all the computers available
in the network.
Partial Mesh Topology: In a partial mesh topology, not all but certain computers are connected to those
computers with which they communicate frequently.
Advantages of Mesh topology:
Reliable: The mesh topology networks are very reliable as if any link breakdown will not affect the
communication between connected computers.
Fast Communication: Communication is very fast between the nodes.
Easier Reconfiguration: Adding new devices would not disrupt the communication between other devices.
Disadvantages of Mesh topology
Cost: A mesh topology contains a large number of connected devices such as a router and more
transmission media than other topologies.
Management: Mesh topology networks are very large and very difficult to maintain and manage. If the
network is not monitored carefully, then the communication link failure goes undetected.
Efficiency: In this topology, redundant connections are high that reduces the efficiency of the network.
Hybrid Topology
The combination of various different topologies is known as Hybrid topology.
A Hybrid topology is a connection between different links and nodes to transfer the data.
When two or more different topologies are combined together is termed as Hybrid topology and if similar
topologies are connected with each other will not result in Hybrid topology. For example, if there exist
a ring topology in one branch of ICICI bank and bus topology in another branch of ICICI bank, connecting
these two topologies will result in Hybrid topology.
Advantages of Hybrid Topology
Reliable: If a fault occurs in any part of the network will not affect the functioning of the rest of
the network.
Scalable: Size of the network can be easily expanded by adding new devices without affecting the
functionality of the existing network.
Flexible: This topology is very flexible as it can be designed according to the requirements of the
organization.
Effective: Hybrid topology is very effective as it can be designed in such a way that the strength of
the network is maximized and weakness of the network is minimized.
Disadvantages of Hybrid topology
Complex design: The major drawback of the Hybrid topology is the design of the Hybrid network. It is
very difficult to design the architecture of the Hybrid network.
Costly Hub: The Hubs used in the Hybrid topology are very expensive as these hubs are different from
usual Hubs used in other topologies.
Costly infrastructure: The infrastructure cost is very high as a hybrid network requires a lot of
cabling, network devices, etc.
Transmission modes
The way in which data is transmitted from one device to another device is known as transmission
mode.
The transmission mode is also known as the communication mode.
Each communication channel has a direction associated with it, and transmission media provide the
direction. Therefore, the transmission mode is also known as a directional mode.
The transmission mode is defined in the physical layer.
The Transmission mode is divided into three categories:
Simplex mode
Half-duplex mode
Full-duplex mode
Simplex mode
In Simplex mode, the communication is unidirectional, i.e., the data flow in one direction.
A device can only send the data but cannot receive it or it can receive the data but cannot send the
data.
This transmission mode is not very popular as mainly communications require the two-way exchange of
data.
The simplex mode is used in the business field as in sales that do not require any
corresponding
reply.
The radio station is a simplex channel as it transmits the signal to the listeners but never allows them
to transmit back.
Keyboard and Monitor are the examples of the simplex mode as a keyboard can only accept the data from
the user and monitor can only be used to display the data on the screen.
The main advantage of the simplex mode is that the full capacity of the communication channel can be
utilized during transmission.
In simplex mode, the station can utilize the entire bandwidth of the communication channel, so that more
data can be transmitted at a time.
Communication is unidirectional, so it has no inter-communication between devices.
Half-Duplex mode
In a Half-duplex channel, direction can be reversed, i.e., the station can transmit and receive the data
as well.
Messages flow in both the directions, but not at the same time.
The entire bandwidth of the communication channel is utilized in one direction at a time.
In half-duplex mode, it is possible to perform the error detection, and if any error occurs, then the
receiver requests the sender to retransmit the data.
A Walkie-talkie is an example of the Half-duplex mode. In Walkie-talkie, one party speaks, and another
party listens. After a pause, the other speaks and first party listens. Speaking simultaneously will
create the distorted sound which cannot be understood.
In half-duplex mode, both the devices can send and receive the data and also can utilize the entire
bandwidth of the communication channel during the transmission of data.
In half-duplex mode, when one device is sending the data, then another has to wait, this causes the
delay in sending the data at the right time.
Full-duplex mode
In Full duplex mode, the communication is bi-directional, i.e., the data flow in both the directions.
Both the stations can send and receive the message simultaneously.
Full-duplex mode has two simplex channels. One channel has traffic moving in one direction, and another
channel has traffic flowing in the opposite direction.
The Full-duplex mode is the fastest mode of communication between devices.
The most common example of the full-duplex mode is a telephone network. When two people are
communicating with each other by a telephone line, both can talk and listen at the same time.
Both the stations can send and receive the data at the same time.
If there is no dedicated path exists between the devices, then the capacity of the communication channel
is divided into two parts.